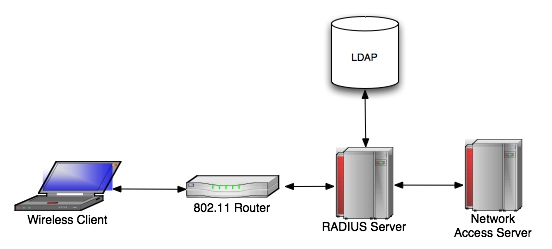
Wireless Authentication SolutionsAuthentication and Access ControlAs is the case with any valuable resource, there must be limitations on who can access and use your wireless medium. In some situations, such as when offering wireless access to attract customers, these limitations will be minimal. In others, we want the greatest possible protection available. Controlling access to computer resources is best illustrated in the AAA framework: Authentication, Authorization, and Accounting. Authentication is the ability to identify a system or network user through the validation of a set of assigned credentials. If you have ever been prompted for a username and password when turning on your computer, you have experienced authentication first hand. Authorization defines the ability of a specific user to perform certain tasks, such as deleting or creating files, after the authentication process has taken place. Finally, accounting allows us to measure and record the consumption of network or system resources. The AAA framework lends itself well (as it does to any computer resource) to wireless network access control. Based on the AAA framework, RADIUS is a popular[1] client\server approach for authenticating remote users. In order to do this, the RADIUS protocol challenges, or prompts, end users for their credentials through a Network Access Server, or NAS. The NAS is actually a client of a RADIUS server, which centrally controls user access to its client?s (the NAS) services. A RADIUS server is responsible for receiving end user requests, authenticating the user, and then providing the NAS with all of the information necessary for it to deliver services. RADIUS can use several Database Management Systems and directory protocols to manage the list of network users and their privileges. As you can see, this method of authentication provides a secure and centralized way to control access to network resources. But what does it have to do with wireless networking? Extensible Authentication Protocol is used by wireless access points to facilitate authentication. When a user requests access to an AP, EAP (if enabled) will challenge the user for his or her identity. EAP then passes the credentials to an authentication server such as RADIUS, which will allow or deny access to its resources. EAP can be easily implemented because it can be used with a back-end authentication server such as RADIUS, and it supports multiple authentication methods such as Kerberos and Public Key Infrastructure (PKI). There are several different types of EAP, which employ different methods of passing authentication information, but for our purposes it is only important to know that EAP is the component of the authentication process that lies on the wireless tier. Lightweight Directory Access Protocol, or LDAP, is a straightforward technology that defines the way information is organized and accessed. As a protocol, it is inherently a set of rules for communication. By implementing LDAP, network administrators can centralize and secure user information for easy management. LDAP can work in conjunction with RADIUS in order to authenticate users. RADIUS, EAP, and LDAP: Solid Wireless Authentication Though there are other solutions for authenticating wireless clients, the combination of RADIUS, EAP, and LDAP is the most common and available solution in use in business today. Each component has associated open-source software that is freely available for network administrators to download, configure, and use. Thus, with the hardware in place, installation of an authentication system is inexpensive.
Other Solutions There are other authentication frameworks and methods that you can employ that will perform in different ways. Another popular method is NoCat[2], which was initially developed as a project for community and as an amateur wireless network authentication scheme that does not require time and resource-consuming RADIUS server and user database setup (Vladimirov, Gavrilenko, Mikhailovsky). NoCat uses a wireless access point and a Linux router or gateway box to control access. Whatever authentication method you decide to employ, if you decide to employ one at all, remember that the number one goal is to protect your valued resources effectively and within your specific business? constraints.
[1] According to SearchSecurity.com RADIUS is ?a de facto industry standard used by a number of network product companies and is a proposed IETF standard? [2] ?Community Supported 802.11b Wireless Network in Sonoma County, CA? http://nocat.net (accessed November 2004). Bron: http://www.invulnerableit.com/modules/news/article.php?storyid=6 |